Cognitive Security in Modern Warfare
Using AI to disclose information manipulation, expose collaborative behaviors, discover the dissemination of malicious information, and identify narrative strategies used by troll account groups.
Uncover and Analyze
Once troll activities are detected, this platform uncovers and provides comprehensive information to display the detailed insights of online malicious actors, hidden agendas, and bot networks operating both on the internet and social media platforms. With the help of aggregated information graphics, enterprises can easily grasp the complex realm of information warfare and understand the impact of the issues.
Recognize information warfare
Access a comprehensive list of active attackers and their targeted events. Gain insights into the specific campaigns conducted by these attacker groups and understand the magnitude of their impact.
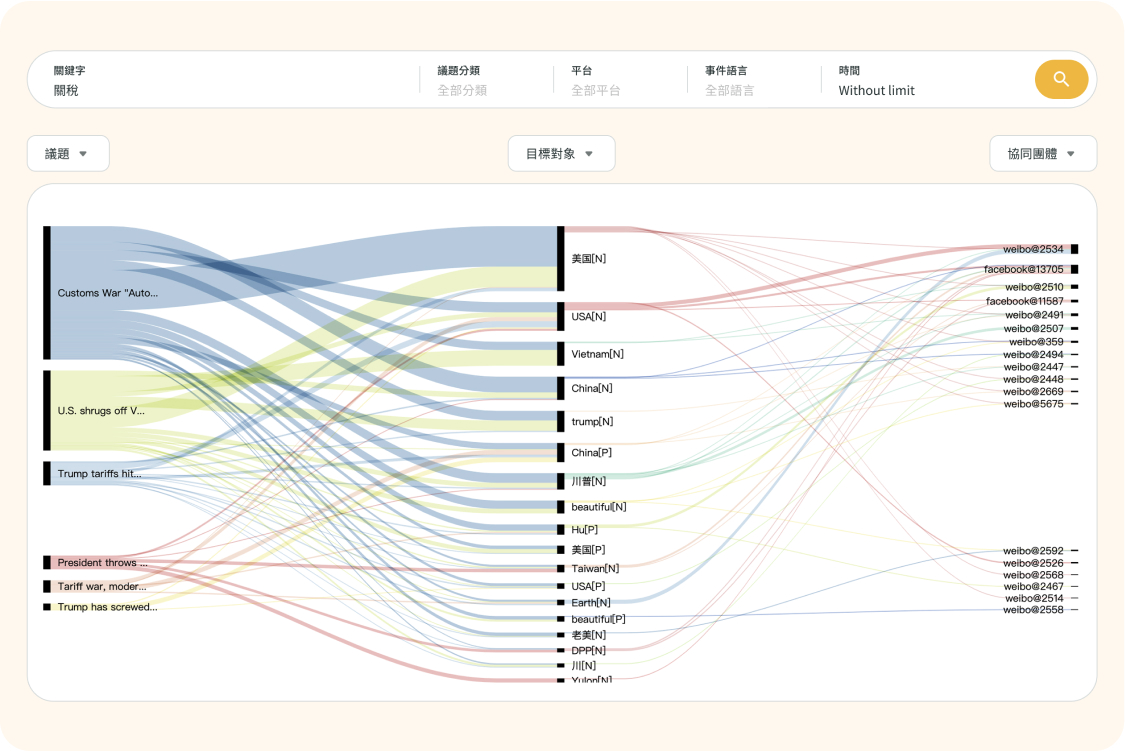
Mastering the warfare
Empower enterprises to track back with a comprehensive view of the evolution of warfare. Explore its origins, the tactics employed by attackers, and the methods they utilized to effectively spread their narratives on a large scale.
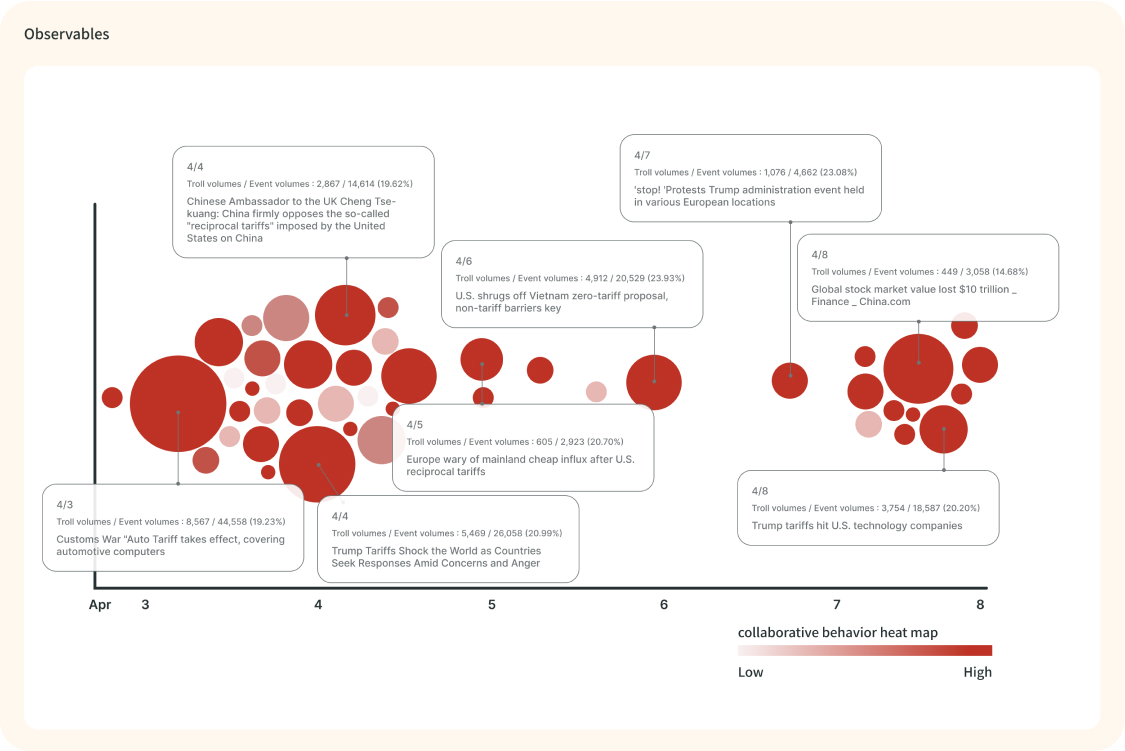
Expose campaigns, targets, tactics and strategies
Drill in and obtain valuable insights of selected events, with the volume of impacts generated by attackers in full degree of major social media views. Understand the attackers’ targets, tactics, and strategies. Stay informed about the development stages of these events.
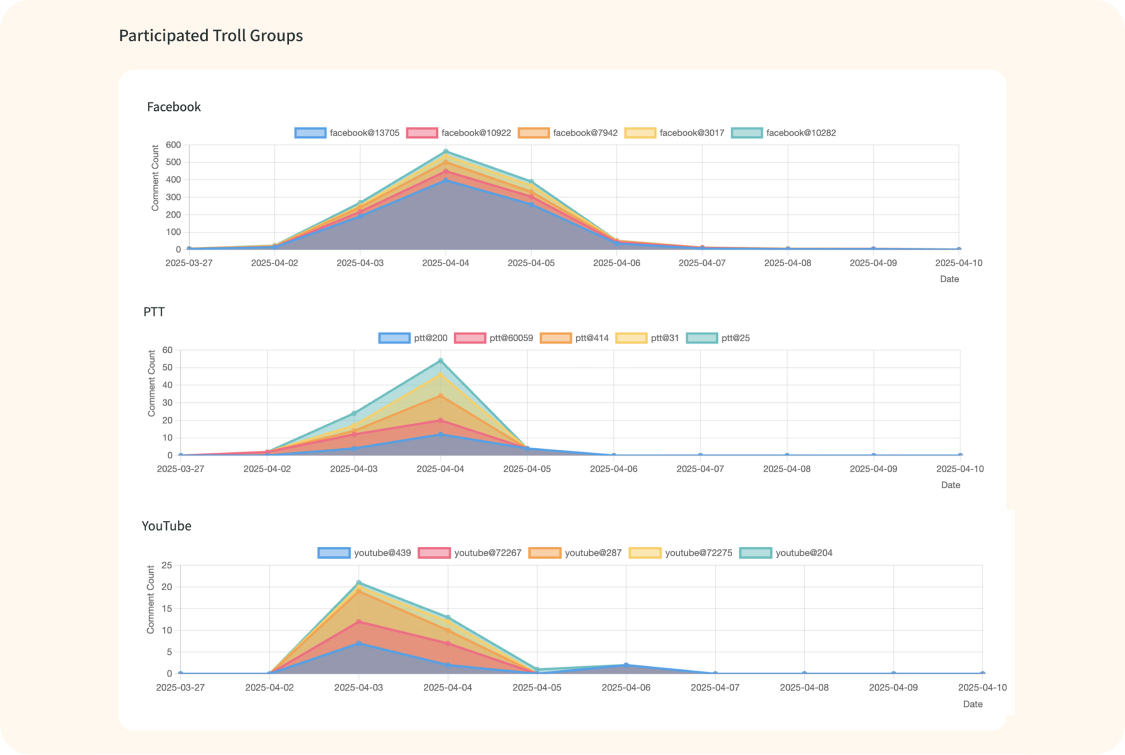
Reveal the attackers
Reveal the comprehensive activity history of the attackers, including the events they have been involved in and their specific targets. Additionally, the system uncover any potential collaborations between these attackers and foreign entities, providing a comprehensive understanding of their operations.
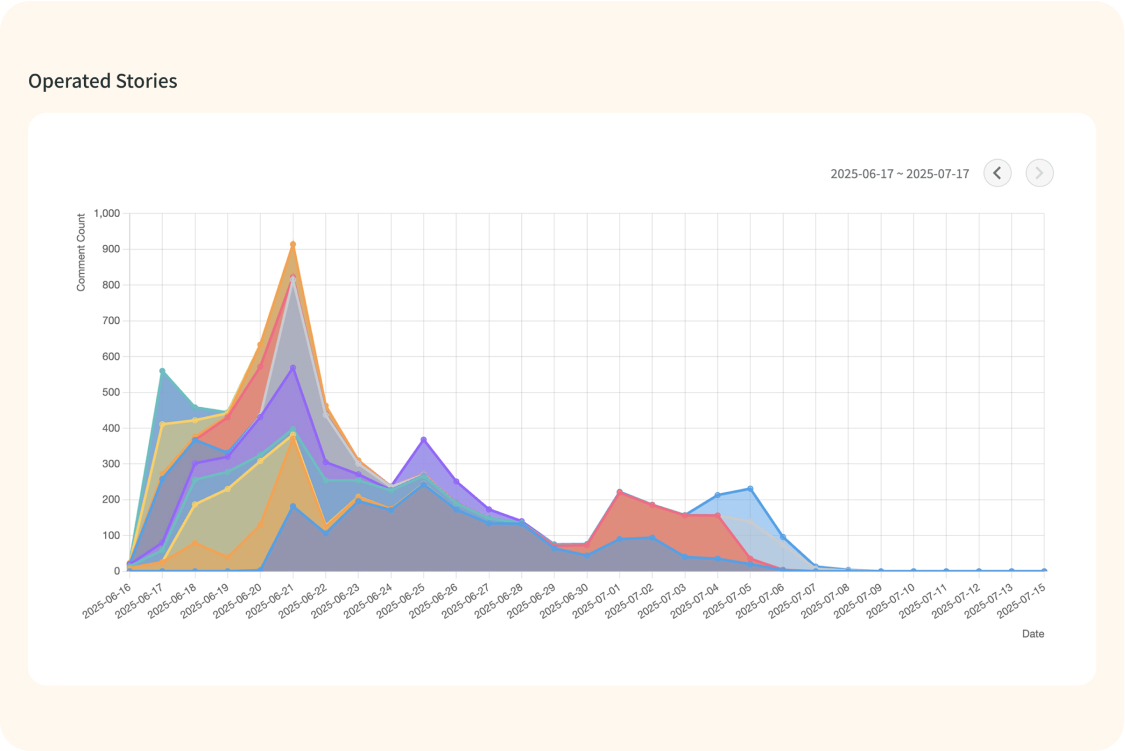
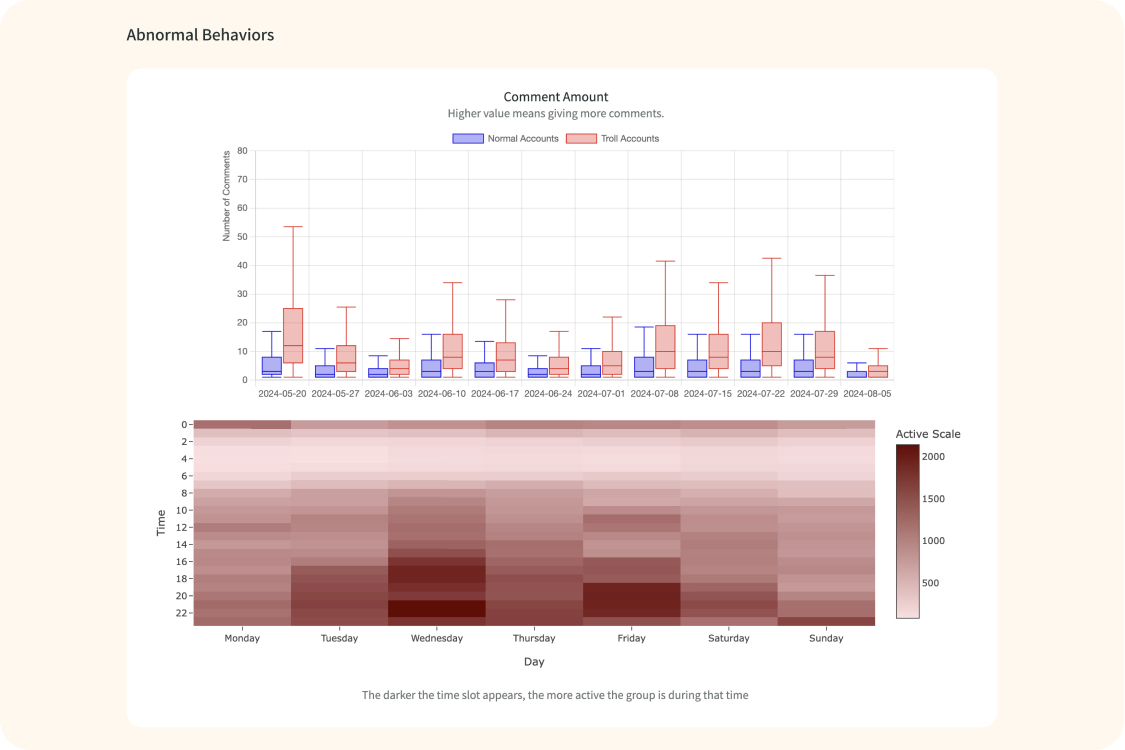
Provide evidence of troll behaviors
Fully analyze the behavior histories and reveals behavioral patterns as solid evidence to distinguish troll account from organic account.
Report and Response
Empower enterprises to thwart attacks by informing individuals about the tactics employed in information warfare through concise summaries of the supporting evidence.
